Protecting Yourself from Phishing Scams
Did you know that 85% of cyber security breaches in 2020 involved “the human element”1 and that the share of phishing-related breaches climbed 11% over the previous year1? For 2019, the FBI Internet Crime Complaint Center received reports from 114,702 people, that lost a combined $57,836,379 to Phishing Scams2 alone.
Overall in 2019, the FBI Internet Crime Complaint Center received 467,361 complaints, with an estimated cost of $3.5 Billion dollars3. And, according to Federal Bureau of Investigation11, “Between May 2018 and July 2019, there was a 100 percent increase in identified global exposed losses” due to Business Email Compromise (spear phishing).
What is Phishing? Vishing? Smishing?
Phishing is when you are contacted “by someone posing as a legitimate institution to lure individuals into providing sensitive data”4. Similarly, the FBI offers definitions of these more specific terms5:
- “Vishing scams happen over the phone, voice email, or VoIP (voice over Internet Protocol) calls.”
- “Smishing scams happen through SMS (text) messages.”
- “Pharming scams happen when malicious code is installed on your computer to redirect you to fake websites.”
A more targeted version of phishing is generally referred to as Spear Phishing. “Spear phishing uses focused, customized content that’s specifically tailored to the targeted recipients (typically, after reconnaissance on the recipients by the attacker).”6
What are phishing scams phishing for?
The short answer: money.
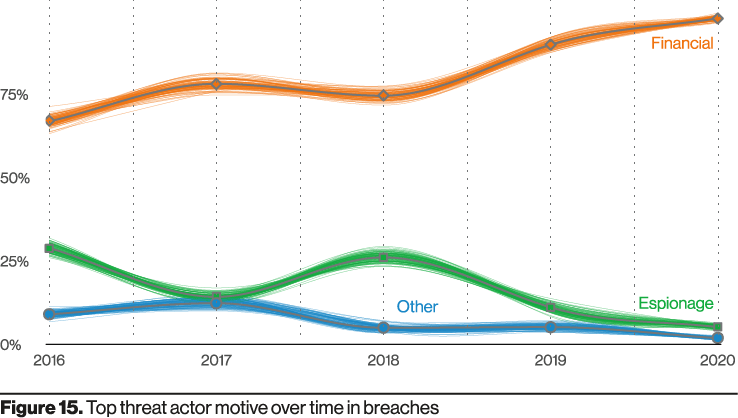
According to the “2021 Data Breach Investigations Report”1, financial motives accounted for the vast majority of cyber breaches in 2020 (Figure 15 above).
Of course, most of the time they are not going to just ask you for money in an email! Instead, they will try and get you to disclose personal information5,7,8 such as Credit card numbers, bank account information, passwords, account numbers, Social Security number, banking PINs, etc. They can then use or sell this information for financial rewards.
How to Recognize Phishing Scams
The 5 most basic ways to recognize phishing scams4, include:
- Too Good to Be True: If an offer seems too good to be true, then it probably is. If you think a good deal is legitimate, then “Look up the company’s phone number on your own (don’t use the one a potential scammer is providing), and call the company to ask if the request is legitimate.”9
- Sense of Urgency: “Be especially wary if the requestor is pressing you to act quickly.”9
- Hyperlinks: “Don’t click on anything in an unsolicited email or text message”9 and “Carefully examine the email address, URL, and spelling used in any correspondence. Scammers use slight differences to trick your eye and gain your trust.”9
- Attachments: “Be careful what you download. Never open an email attachment from someone you don’t know, and be wary of email attachments forwarded to you.”9
- Unusual Sender: If you don’t know the sender’s email address, then that’s a huge red flag that something is wrong. “Carefully examine the email address, URL, and spelling used in any correspondence. Scammers use slight differences to trick your eye and gain your trust.”9
How to Protect Yourself from Phishing
There are a few ways you can help be better protected from phishing scams. These include making sure you have automatic updates and multi-factor authentication turned on. According to the Federal Bureau of Investigation10, there are 4 steps to protect yourself from phishing:
- “Protect your computer by using security software.” This includes making sure it is updating and running automatically (without your intervention).
- “Protect your mobile phone by setting software to update automatically.”
- “Protect your accounts by using multi-factor authentication.”
- “Protect your data by backing it up. Back up your data and make sure those backups aren’t connected to your home network. You can copy your computer files to an external hard drive or cloud storage. Back up the data on your phone, too.” If your backups are corrupted, then you don’t have backups.
While there are IT considerations in a cyber security breach, with 85% of cyber security breaches in 2020 having involved “the human element”1, the largest share of the threat falls on user judgement.
For that reason, everyone, including business leaders, and other valuable targets should make sure themselves and their employees are familiar with some examples and what to look for. The Federal Bureau of Investigation has these short examples of real scams9:
In a BEC scam, criminals send an email message that appears to come from a known source making a legitimate request, like in these examples:
- A vendor your company regularly deals with sends an invoice with an updated mailing address.
- A company CEO asks her assistant to purchase dozens of gift cards to send out as employee rewards. She asks for the serial numbers so she can email them out right away.
- A homebuyer receives a message from his title company with instructions on how to wire his down payment.
Versions of these scenarios happened to real victims. All the messages were fake. And in each case, thousands—or even hundreds of thousands—of dollars were sent to criminals instead.
Talk about a way to quickly ruin your day!
Finally, if you spot a phishing scam, report it to the Federal Trade Commission:
Step 1. If you got a phishing email, forward it to the Anti-Phishing Working Group at reportphishing@apwg.org. If you got a phishing text message, forward it to SPAM (7726).
Step 2. Report the phishing attack to the FTC at ReportFraud.ftc.gov.
If in doubt, don’t click!
I’ve written before about Recognizing Scams and I recommend reading it for a step-by-step guide to go through a potentially phishy message.
The bottom line really is, if you are at all unsure about any message, it is strongly recommended that you call a business from the phone number listed on their main website (search for it, do not click any links), and ask them directly.
Finally, here is a quiz from the Federal Trade Commission about phishing. Test your phishing knowledge!
What phishing scams have you seen? Tell us about it in the comments.
References and Further Reading
- (2021). 2021 Data Breach Investigations Report. Retrieved July 7, 2021, from https://www.verizon.com/business/en-au/resources/reports/dbir/.
- Federal Bureau of Investigation. (2020). 2019 Internet Crime Report. Retrieved July 7, 2021, from https://www.ic3.gov/Media/PDF/AnnualReport/2019_IC3Report.pdf.
- Federal Bureau of Investigation. (2020, February 11). 2019 Internet Crime Report Released. Retrieved July 7, 2021, from https://www.fbi.gov/news/stories/2019-internet-crime-report-released-021120.
- (n.d.). What Is Phishing. Retrieved July 7, 2021, from https://www.phishing.org/what-is-phishing.
- Federal Bureau of Investigation. (n.d.). Spoofing and Phishing. Retrieved July 7, 2021, from https://www.fbi.gov/scams-and-safety/common-scams-and-crimes/spoofing-and-phishing.
- (2021, June 22). Anti-phishing protection in Microsoft 365. Retrieved July 7, 2021, from https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/anti-phishing-protection?view=o365-worldwide.
- (n.d.). Protect yourself from phishing. Retrieved July 7, 2021, from https://support.microsoft.com/en-us/windows/protect-yourself-from-phishing-0c7ea947-ba98-3bd9-7184-430e1f860a44.
- Federal Trade Commission. (n.d.). How to Recognize and Report Spam Text Messages. Retrieved July 7, 2021, from https://www.consumer.ftc.gov/articles/how-recognize-and-report-spam-text-messages.
- Federal Bureau of Investigation. (n.d.). Business Email Compromise. Retrieved July 7, 2021, from https://www.fbi.gov/scams-and-safety/common-scams-and-crimes/business-email-compromise/.
- Federal Trade Commission. (n.d.). How to Recognize and Avoid Phishing Scams. Retrieved July 7, 2021, from https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams.
- Federal Bureau of Investigation. (2019, September 10). Business Email Compromise The $26 Billion Scam. Retrieved July 7, 2021, from https://www.ic3.gov/Media/Y2019/PSA190910.
- Brooks, C. (2021, March 2). Alarming Cybersecurity Stats: What You Need to Know for 2021. Retrieved July 7, 2021 from https://www.forbes.com/sites/chuckbrooks/2021/03/02/alarming-cybersecurity-stats——-what-you-need-to-know-for-2021/?sh=5d73e49658d3.
- (n.d.). Social Engineering. Retrieved July 7, 2021, from https://www.knowbe4.com/what-is-social-engineering/.
- (2017, February 10). Best Practices: Identifying and Mitigating Phishing Attacks. Retrieved July 7, 2021, from https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/best-practices-identifying-and-mitigating-phishing-attacks.
- Federal Trade Commission. (n.d.). Phishing Quiz. Retrieved July 7, 2021, from https://www.ftc.gov/tips-advice/business-center/small-businesses/cybersecurity/quiz/phishing.



